Install OpenSSL for Windows. Once accomplished, you have the openssl.exe executable somewhere on your system.
Now proceed as follows.
openssl pkcs12 -in avatar.pfx -out avatar.pem -nodes
(You need to enter the .pfx password here)
openssl pkcs12 -in avatar.pfx -out mycert.pem -nodes -clcerts
(again the PW)
openssl x509 -in mycert.pem -out mycert.cer -outform DER
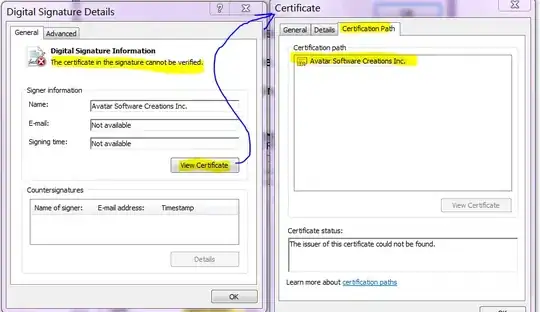
Now open your Explorer and double-click on the mycert.cer. View the details and somewhere it will talk about an issuer. This is the company that issued your key store, your next goal is to get their intermediate certificates and the final root certificate. If you are lucky, there is an extension called "Authority Information Access" in your certificate that tells you where to get the issuing certificate directly. If you are not so lucky, then you will find a URL for OCSP access in the "Authority Information Access" or a URL for CRLs in the extension "CRL Distribution Points". These should at least give you a vague idea of the vendor's "homepage". In case of doubt, just google around, or ask me again :)
If you are on the vendor's page, you will have to watch out for "CA certificates" or "Intermediate Certificates". You need to download the one whose name is exactly the same as what you found in the "Issuer" field of your own certificate.
Now the funny part: The certificate you just found will again have an "Issuer" field. Lucky you if the issuer is the same company (typically the case for large CAs such as VeriSign), then you will find the corresponding certificate on the same site you are currently on. If not, repeat the previous steps.
Repeat this cumbersome procedure until you're at a point where you have found a certificate whose "Subject" field is exactly the same as its "Issuer" field. You're done then. This is a so-called "self-signed root certificate".
Most of these certificates will come in "DER"/"ASN.1"/"X.509" format - if you have the choice, download "PEM" format, otherwise you will first need to convert the certificates into "PEM" format by
openssl x509 -in cert.der -inform DER -out cert.pem
Once you have all the missing certificates in PEM format
open the initial file created in step 1, avatar.pem, in a text editor.
open the missing certificate PEM files in separate windows
copy the missing certificates (the entire file, including the "----- BEGIN CERTIFICATE -----" and "----- END CERTIFICATE -----") and append them to avatar.pem
save the result
issue
openssl pkcs12 -export -in avatar.pem -out newavatar.pfx -name ""
You will have to enter a new password that is to be used with the new file.