- The proof of Theorem 5.2.13 : For semantic security, the author wrote "$m_1 \leftarrow {\rm Sim_1}(1^\lambda)$". I think it may contradict with the security requirement defined in Definition 5.2.11 and Definition 5.2.12 where it is required that the outputs of ${\rm Sim_1}(1^\lambda)$ and ${\rm SFE1_F}(1^\lambda, x)$ should be indistinguishable, that is, it should be "$(s, m_1) \leftarrow {\rm Sim_1}(1^\lambda)$" instead of "$m_1 \leftarrow {\rm Sim_1}(1^\lambda)$".
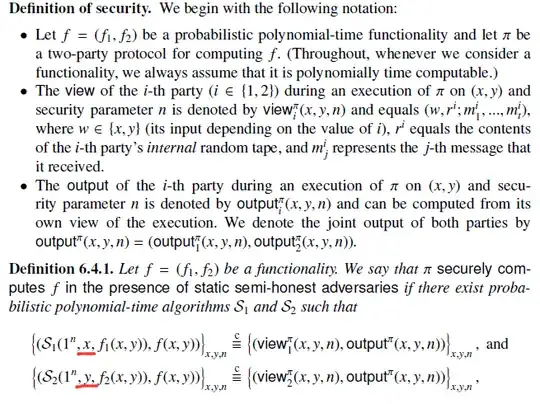
- Definition 5.2.12 : The secret inputs y and x are not provided to the simulators ${\rm Sim_1}$ and ${\rm Sim_2}$. I think it may contradict with Definition 6.4.1, where the secret inputs are required to be provided to the simulators.
- Definition 5.2.11 and Definition 5.2.12 : Does ${\rm F}(x, y) = {\rm SFE3_F}(s, m_2)$ hold if $(s, m_1)$ is generated by using ${\rm Sim_1}$ and $m_2$ is generated by using ${\rm Sim_2}$?
Tutorials on the foundations of cryptography: dedicated to Oded Goldreich: https://lib.ugent.be/en/catalog/ebk01:3850000000027399#:~:text=00000nam%20a22000005i%204500%20%20%20001%20%20,%7C%7C%7C%7C%200%7Ceng%20d%20%2036%20more%20rows%20