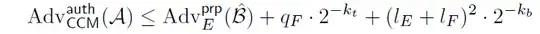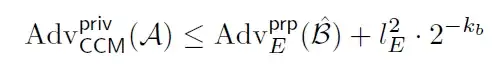CCM mode refers to CTR+ CBC-MAC encryption mode.
Based on this paper, the adversary's advantages against the authenticity of CCM is:
Authenticity: it should be infeasible for an adversary to forge a valid ciphertext without knowing the secret key.
and the adversary's advantage against the privacy of CCM is:
Privacy: It should be infeasible for an adversary to derive any information from the ciphertexts without knowing the secret key.
I'm confused about "derive any information from the ciphertexts" in the definition of privacy shown above. Does it mean if privacy is broken, the adversary is able to derive plaintext information from the ciphertext? If so, complete infomation about plaintext or only partial information about plaintext? But I also feel that Eq(2) describes the advesary's ability of differentiating cipertext of CCM from random bitstring, so we are not able to know the plaintext even if privacy is broken.
My second question is about the authenticity. Will break the authenticity lead to leakage of plaintext? In other words, if we want to proof the privacy of the plaintext, do we need to consider the case that the authenticity is broken?
Thank you in advance.
Note: Adv_E^prp(B) is the adversary's advantage on pseudo random permutation (prp).