Will this encryption scheme have its security according to the key length? Will I have 8192-bits of encryption strength?
No, the security is limited with
$$security = min\{\text{Argon2 input_size}\;, \;\text{Hash digest size}\}$$ In your case with BLAKE2-512, it is 512-bit security not 8192.
The reason is clear. Argon2 returns return Hash(C, tagLength) (variable-length hash function) or see from Argon2 paper page 6 *
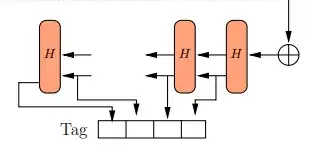
And if BLAKE2 is used then the first 64 byte is the output of the BLAKE2. If the output requirement is > 64 bytes, then the remaining bytes are derived from the output of the previous BLAKE2 calls.
V1 ← Blake2b(digestSize ∥ FinalBlock, 64);
Subsequent blocks are generated from previous blocks
for i ← 2 to r do
Vi ← Blake2b(Vi-1, 64)
Lower 32 bytes of Vi is returned.
Therefore one cannot have security larger than the hash digest size and this should be enough for even post-quantum adversaries.
And, 256-bit security is enough for everybody. Argon2 is designed for Password hashing, although one can use this for CTR mode, still prefer the xChaCha20-Poly1305 to get confidentiality, integrity, and authentication. This is much faster than Argon2 for encryption. The xChaCha20 is the extension of ChaCha20 with 192-bit nonces that enables random nonces without fear of nonce reuse problem of the CTR mode.
* The default output only outputs single hash. This enables Client Independent Update is a functional requirement of the password hashing competition.
