While it possible to construct a stream cipher from a hash function. This construction has one very serious flaw.
The largest issue is you have no nonce so if your key is reused it becomes trivial to decrypt both messages since your just xor-ing the plaintext.
What you effectively has is the following per block:
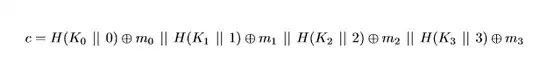
Further, you will not get 2048 bits of encryption here. For instance I could attack the first 512 bits of cipher the text. Which means I only have to find the first key. Same for the second key ect... So for the entire block your only having to find 4 keys. So you effectively only increased the key length by 2 bits. This is because each key is independent of the other so in a brute-force attack changing one does not effect the other keys. So if your goal was 2048 bits of key strength it's even worse than a meet in the middle attack. It's basically only as strong as your starting keys bit length.
Also such a large key is kinda pointless for symmetric ciphers.
The post quantum security of hash functions like BLAKE2b are already quite secure especially with a 512 bit digest.