I found only the abstract and tables of this paper https://dl.acm.org/doi/abs/10.1145/3409501.3409513
From the abstract
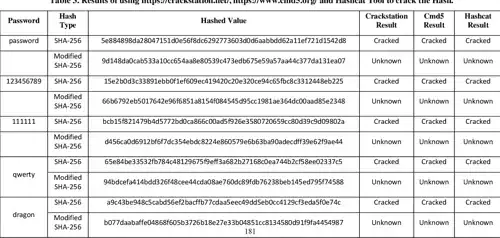
In this paper, the researchers proved that the modified SHA256 is viable to length extension, brute-force and dictionary attacks. Randomness tests also showed uniform random distribution of the hashes generated by the modified SHA256
The meaning of each randomness test:
Monobit https://www.random.org/statistics/frequency-monobit/ Per block https://www.itl.nist.gov/div898/software/dataplot/refman1/auxillar/freqtest.html runs test https://www.investopedia.com/terms/r/runs_test.asp
Does anyone have a full copy of it?
& Do you have any comments about it's impact on the strength of all SHA-256 dependant systems? (cryptocurrencies for example)
Ps
I should've clarified that modified SHA-256 is supposed to have more cryptographic strength (as the 2nd table above shows). It was published in IEEE 2018
https://www.semanticscholar.org/paper/Modified-SHA256-for-Securing-Online-Transactions-on-Perez-Gerardo/d69b7c800dcf9373b6bf1a5111b1dc5d3bf077f4#extracted https://www.researchgate.net/publication/331747184_Modified_SHA256_for_Securing_Online_Transactions_based_on_Blockchain_Mechanism
This research is composed of online transaction security; the mechanism of blockchain and proposed a modified SHA256 security protocol through smart contract to secure online transaction procedure specifically based on Blockchain Mechanism. It focus on the discussion of modifying security protocol specifically designed for practical applications of blockchain with particular reference to privacy and trust. The researcher recommend a new transaction procedure involving customer and merchant, permitting entities to recognize one another enabling them to proceed with their transactions securely using Blockchain Mechanism
(it is a very well known fact that both IEEE & ACM are from the very top respectable conferences & journals)
Another HAI paper, Mar21, that gives an idea on how fast a brute force attack can be (although repeating that their results doesn't weaken SHA-256, however they also say that the rank of the Super Computer they used changed from 29th when they started to 463th now?!)
https://hal.archives-ouvertes.fr/hal-02306904v2
used https://github.com/bitmaintech/cgminer https://github.com/pooler/cpuminer