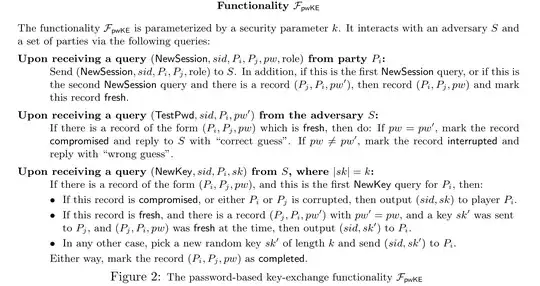
The question is essentially why the line
If this record is compromised, or either $P_i$ or $P_j$ is corrupted, then output $(sid, sk)$ to player $P_i$.
is used in the ideal functionality, rather than
If this record is compromised, $P_i$ is corrupted, or $P_j$ is corrupted and there is a record $(P_j, P_i, pw')$ with $pw' = pw$, then output $(sid, sk)$ to player $P_i$.
This change would make it clear that a malicious user $P_j$ cannot successfully run this protocol to log in to an honest server $P_i$ if it makes an incorrect password guess, even when there is no man-in-the-middle (MITM) attack.
I still do not know the reason for the current ideal functionality, but I do know that it is equivalent to the proposed modification when the underlying communication ideal functionality allows MITM attacks.
In particular, I will assume that the PAKE, like every PAKE I know of, is based on the unauthenticated channel functionality, where the adversary is allowed to view all of the messages and modify them arbitrarily.
Let $\newcommand\oldfunc{\mathcal{F}}\oldfunc$ be Canetti et al.'s ideal functionality, $\newcommand\newfunc{\mathcal{F}'}\newfunc$ be the modified ideal functionality, and $\newcommand\commfunc{\mathcal{F}_{UA}}\commfunc$ be the unauthenticated channel functionality.
Assume there is a protocol $\newcommand\prot{\mathcal{P}}\prot$ that realizes $\oldfunc$ in the $\commfunc$-hybrid model, using a simulator $\newcommand\oldsim{\mathcal{S}}\oldsim$.
Then there is a simulator $\newcommand\newsim{\mathcal{S}'}\newsim$ that shows that $\prot$ realizes $\newfunc$ in the $\commfunc$-hybrid model.
If both $P_i$ and $P_j$ are corrupted, or neither are, then $\newfunc$ behaves identically to $\oldfunc$, so $\newsim$ can behave exactly the same as $\oldsim$ in this case.
If there is one honest party $\newcommand\honP{P_i}\honP$ and one corrupted party $\newcommand\corP{P_j}\corP$, then $\newsim$ imagines a scenario where $\honP$ is still present, but also there is a second honest party $\newcommand\imagP{P_k}\imagP$ and a MITM attacker $\newcommand\mitmP{P_j'}\mitmP$.
Specifically, $\imagP$ inputs a uniformly random string in $\{0,1\}^\kappa$ as its password, and the MITM attacker $\mitmP$ drops and ignores all messages from $\imagP$, instead sending all messages from $\honP$ to the original dishonest party $\corP$ and vice versa.
$\newsim$ asks $\oldsim$ to simulate the environment's view for this scenario.
It then forwards $\oldsim$'s queries to the ideal functionality, except that all queries mentioning the imagined honest party $\imagP$ are ignored, replaced with replies of "wrong guess" in the case of $\newcommand{\ucsymbol}[1]{\textsf{#1}}\ucsymbol{TestPwd}$ queries.
For the proof of indistinguishability (in the case of one honest party and one malicious party) between the real protocol $\prot$ that uses the communication functionality $\commfunc$, and the ideal functionality $\newfunc$ composed with the simulator $\newsim$, consider the following hybrids, starting from the real world.
- Introduce a new party $\imagP$ that runs the real protocol with $\honP$ honestly, using a password sampled uniformly randomly from $\{0,1\}^\kappa$, though all of its messages are blocked in both directions. This is indistinguishable because this new party has no interaction with anything at all.
- Reinterpret this interaction as being the execution of $\prot$ between two honest parties, but with a MITM attacker $\mitmP$ blocking the messages and behaving as described in $\newsim$. This is just a change of perspective, nothing actually changed.
- Use the security of $\prot$ as an implementation of $\oldfunc$ between the parties $\honP$ and $\imagP$ to switch from the real protocol to the ideal world, where there is a simulator $\oldsim$ composed with an ideal functionality $\oldfunc$.
- Swap ideal functionalities from $\oldfunc$ to $\newfunc$. This change is indistinguishable because the modification to the ideal functionality is only in the case where one party is compromised, and neither $\honP$ nor $\imagP$ is compromised.
- Delete the imagined honest party $\imagP$. This eliminates a record from the ideal functionality, so $\oldsim$'s corresponding $\ucsymbol{TestPwd}$ queries should be handled by replying "wrong guess", and similarly any corresponding $\ucsymbol{NewKey}$ queries should be ignored. This is indistinguishable because $\oldsim$ has negligible chance of guessing $\imagP$'s password as it was sampled uniformly at random, and the output of a $(\ucsymbol{NewKey}, sid, \imagP, sk)$ query only goes to $\imagP$, which is being deleted. The only other way this might affect the execution is during a $(\ucsymbol{NewKey}, sid, \honP, sk)$ query, but again this would require $\imagP$'s password to be guessed.
- Relabel $\imagP$ with $\corP$. Since $\imagP$ is only mentioned when $(\ucsymbol{NewSession}, sid, \honP, \imagP, pw, role)$ is queried by $\honP$, this change is purely internal to the honest party and the ideal functionality, and cannot be distinguished.
After these hybrids, we are now at the ideal world where the simulator $\newsim$ is composed with the ideal functionality $\newfunc$ in order to generate the view of the environment.