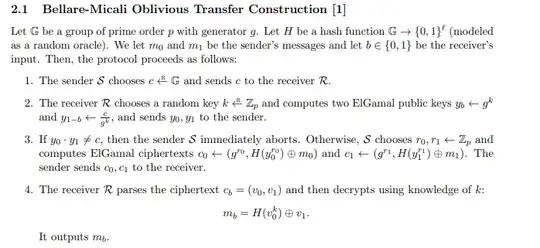
The idea of the Bellare-Micali Oblivious Transfer Constructions is the following:
Informally, the receiver is required to generate two public keys $y_b$, $y_{b-1}$ such that it knows only the secret key paired with $y_b$ (where $b$ is its choice bit), indicated with $k$. In order to prevent the receiver from cheating, the sender requires that the two generated public keys have to satisfy a certain constraint, i.e., $y_b \cdot y_{b-1} = c$ . In such a way, the receiver cannot know both private keys or it can compute DLOG. At this point, the receiver sends the two public keys to the sender. Then, the sender encrypts $m_0$ with $y_0$ and $m_1$ with $y_1$ and sends both encryptions $c_0$, $c_1$ to the receiver. Finally, the receiver obtains $m_b$ by decrypting the chipertext $c_b$ (corresponding to its choice bit) using the private key $k$ (note that $c_b$ is the only chipertext it can decrypt).
While the general idea is clear to me, I do not get why ElGamal is not computed as $y_{0}^{r_{0}} \cdot m_{0}$ (and $y_{1}^{r_{1}} \cdot m_{1}$) but $H(y_{0}^{r_{0}}) \oplus m_{0}$ is used instead.