This is a form of the Kerberos protocol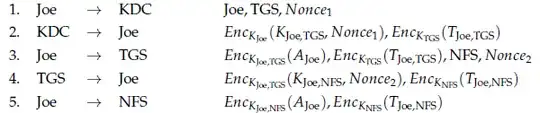
I have two questions. Why does this protocol give the opportunity of a known plain-text attack because of no authentication of Joe? And how would an attacker perform a known plain-text attack?
This is a form of the Kerberos protocol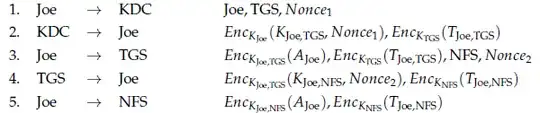
I have two questions. Why does this protocol give the opportunity of a known plain-text attack because of no authentication of Joe? And how would an attacker perform a known plain-text attack?