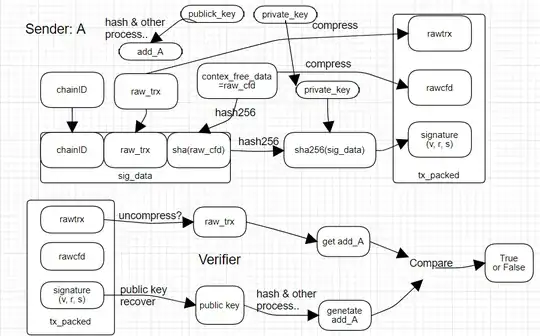
I have been studing ECDSA signature/verify for a while. By my understanding: the standard ECDSA signature/verify process (which we find on text book) are like below:
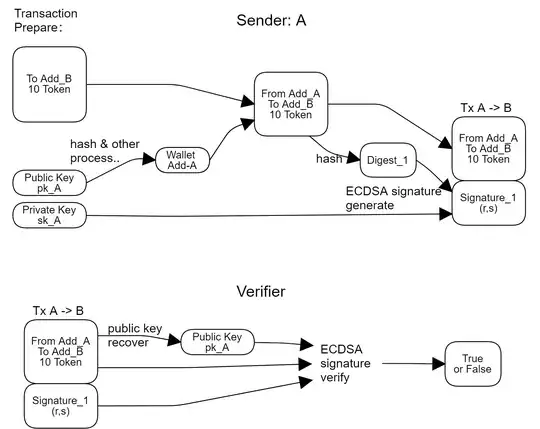 - A sender combines message and its ECC public key (pk), do hash, then using ECC sk (private key) to generate signature; it then append the signature with the message (ECC pk include), send all these to receiver;
- A sender combines message and its ECC public key (pk), do hash, then using ECC sk (private key) to generate signature; it then append the signature with the message (ECC pk include), send all these to receiver;
- The receiver do ECDSA verify by using the ECC pk, the message and the signature output true or false;
Question1: for EOS signature verify process looks not likely align to a standard ECDSA signature verify above:
A EOS node may need do two kinds of ECDSA signature verify:
1). Check each Tx signature--from code it use a routine naming as get_signature_keys, indicate it recovers the pk? Then follow up by a routine naming as check_authorization (this does not like a real signature verification, I couldn't understand what a "check authorization" means--by all mean it does not like a signature verify);
2). Check a Block's signature, this routine (name as "verify_signee") however, looks likely a real ECDSA signature verify.
Question2: I know BTC/ETH may adopt quite different method as they are PoW so each miner must do signature verification for each Tx inside a block, but as they have much more time (several minutes) than in EOS, they would be using the standard ECDSA verification?