Preliminaries
Let $p$ be a safe prime number. Let $\mathbb{Z}_p^*$ be the multiplicative group of integers modulo $p$. We have $\mathbb{Z}_p = \{\,a \in \mathbb{Z} \mid 1 \le a \lt p\,\}$ .
Let $g \in \mathbb{Z}_p$ be a primitive element of $\mathbb{Z}_p$ . Let $h$ be an element of $\mathbb{Z}_p$ .
We define the Discrete Logarithm Problem for a group of integers modulo a Safe prime (DLPS) as:
DLPS: Find the integer $k$ such that $\;\;1 \le k \lt p\;\;$ and $\;\;g^k \equiv h \pmod p$ .
We assume that the best algorithm to solve DLPS is the Number Field Sieve for Discrete Logarithms, which has an expected running time of $$L_p\left[1/3, \sqrt[3]{64/9}\right] \,=\; e^{\textstyle \left(\sqrt[3]{64/9}+o(1)\right)\big(\ln p\big)^{1/3}\big(\ln \ln p\big)^{2/3}}$$
Questions
If we choose $p$ to be a 2048-bit safe prime, which is at least equal to $2^{2047}$, then the expected number of arithmetic operations needed to solve DLPS is approximately equal to:
$$e^{\textstyle \left(\sqrt[3]{64/9}+o(1)\right)\big(\ln 2^{2047}\big)^{1/3}\big(\ln \ln 2^{2047}\big)^{2/3}} \\ \approx \, e^{\textstyle \big(1.923\big)\big(1419\big)^{1/3}\big(7.258\big)^{2/3}} \\ \approx \, e^{\textstyle \big(1.923\big)\big(11.24\big)\big(3.749\big)} \\ \approx \, e^{\textstyle \big(81.00\big)} \\ \approx \, 2^{116.9}$$
Is it correct?
Should I make sure that $(p+1)$ has a large prime factor? (to make $p$ a strong prime)
If I am not mistaken, this is the graph showing the security level of DLPS in function of the size of $p$:
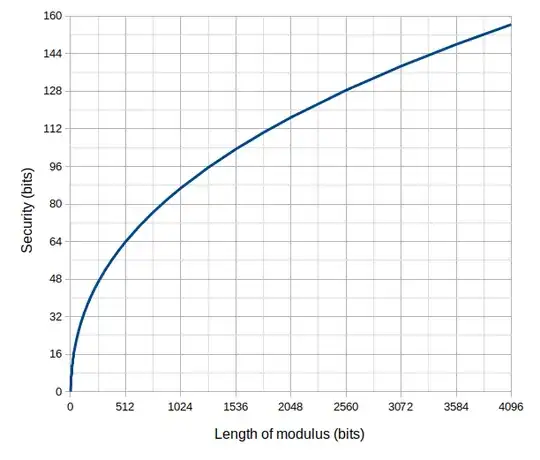
Edit 7th June 2019: Here is the context in which I will use this discrete logarithm problem:
Context
I am creating an online massively multiplayer video game. In this game, the player moves around a character and performs actions in a persistent virtual world. I use the discrete logarithm problem as an in-game currency. Every action performed by a character (move around, buy an item, throw a projectile, etc.) has to be paid by the player with CPU time. This way, I don't have to spend my time monitoring players to detect cheaters (multiple accounts, farming bots, etc), because what cheaters usually do is explicitly allowed in my game.
Here is how it works: to earn the right to perform an action in the virtual world, the player requests a discrete logarithm challenge to the game server. Then, the server generates random values for the generator $g$ and the exponent $k$, computes the result $h \equiv g^k \pmod p$, and send the values of $g$ and $h$ to the player. Then the player's client computes the value of the exponent $k$ and send it back to the server to receive credits.
The value of $p$ will never change, and the values of $g$ and $k$ will be different for each challenge. The player can choose the difficulty of the challenge by setting an upper bound on the bit-length of the value of the exponent $k$ (the amount of credits earned is proportional to the amount of CPU time spent).