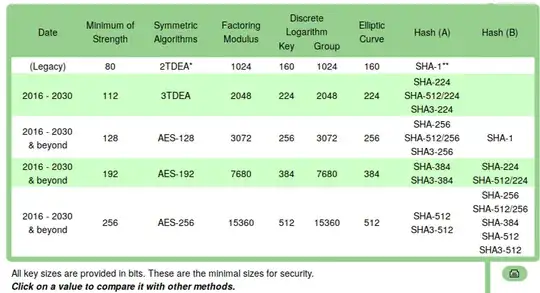
You are already well on your way if you've found https://keylength.com. It references the documents that the recommendations are based on, so if you need a more clear reason to go for a specific key size then you could simply dig deeper. And yes, you need to look at Elliptic Curve sizes for ECDSA.
Using different key sizes for different purposes is spot on. Kelalaka pointed to an interesting document NIST Special Publication 800-57 Part 3
Revision 1: Recommendation for Key Management
Part 3: Application-Specific Key Management Guidance in the comments.
For application for non-repudiation I would go for P-384 or P-521 though, not P-256 or P-384 as indicated in that document. These are signatures that should be made to last. I also think the recommendation to choose an RSA 2048 bit key - a key that has significantly less security than the EC P-256 counterpart in that document - is dangerous for legislative reasons amongst others.
Maybe after 2030 we should worry about quantum computers. You'd better store it at a notary or another third party who can additionally sign the document with post-quantum crypto once (and if) PQC becomes a requirement. If you cannot choose a quantum-safe cryptographic algorithm then choosing RSA - at keysizes of 4096 or over - may give you more breathing room than Elliptic Curve Cryptography.
For real time authentication - the other major use case of ECDSA - you could go for P-256 or a similarly sized curve. However, if your systems can handle it, you might as well use a larger key size - if just to give you some leeway.
Update 2025: quantum secure algorithms such as ML-DSA have been defined. There is more progress around quantum computers, for best security I'd still think that 2030 is the earliest date that we might see a somewhat practical quantum computer. As for Elliptic Curve, NIST has recognized Ed25519 and Ed448.
Beware: in the end the protocol and implementation security are endlessly more likely to be an issue than key size. Too often the key size debate is only important to the sales department and management - mainly because it is really the only thing they kind-of understand.