As the other answers have mentioned, you basically have no hope of executing a key-recovery attack. This does not mean, however, that you should give up and go home. Key recovery is not the only kind of attack, and the information you have available gives you a different attack, which allows you to decrypt some ciphertexts without using the key. The other answers don't mention the fact that this encryption scheme uses ECB-mode.
As you mentioned in a comment, you have a list of valid and related plaintext/ciphertext pairs, and you have another ciphertext, and you want to make an educated guess as to its corresponding plaintext.
The use of ECB mode gives us a credible attack. Recall the operation of ECB:
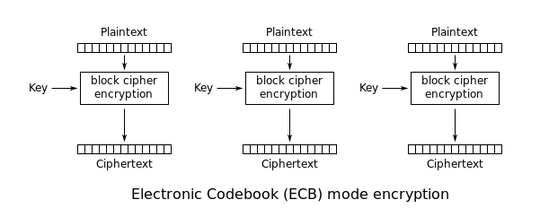
Each plaintext block is fed into the block cipher, and the corresponding ciphertext block is just its output. This means that, wherever the plaintext block appears in whichever message, the output ciphertext will always be identical.
AES usually uses a 128-bit block-size, which is 16 bytes. You might have 192- or 256-bit AES, but I don't see these quite so often. This means that if you split your plaintexts and ciphertexts into 16-byte chunks you might see see that in one chunk the plaintext 11 22 33 44 55 66 77 88 99 00 aa bb cc dd ee ff corresponds to the ciphertext 12 34 56 78 90 ab cd ef fe dc ba 09 87 65 43 21. Now, whenever you see that ciphertext in any message ever, you can map it back to that plaintext!
Now, you mentioned that this was a homework question. You should write some software to do this for you, and exactly what that looks like I'm not going to say because we aren't a homework solving service, but hopefully you should be able to use this insight to recover your flag.
Your next lessons are probably going to talk about CTR and CFB encryption modes, which stop this attack from working.
