Or, you try to cash in on it.
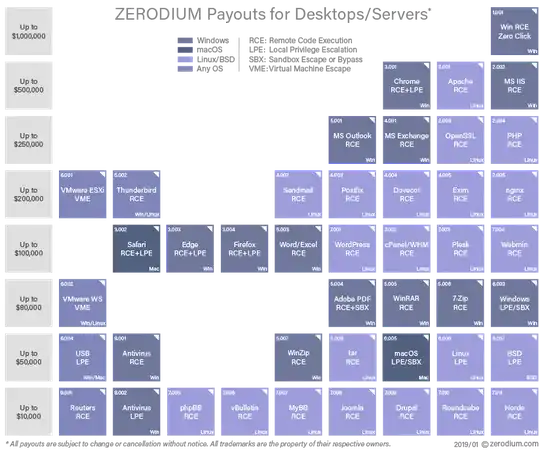
If you're any good at finding flaws, there is a lucrative (and legal) yet very grey market in vulnerabilities and zero day exploits. The New York Times have listed some prices and companies that resell these. Outfits like Zerodium in Washington; Netragard in Acton, Mass.; Exodus Intelligence in Austin, Tex.; and ReVuln, and a Virginia start-up named Endgame. Typical exploits sell for 35,000 to 160,000 dollars, but you can get up to 500,000 dollars for Apple’s iOS.
All of the security agencies pay to get these, presumably under some form of non disclosure agreements/secrecy legislation. The NSA seems to be the largest client, but the FBI also buys exploits such as for back dooring Firefox/Tor. If you're really good, you should be able to sell the same exploit to multiple buyers. It depends on your contacts as to whether you are able to access this market though.
In the war on terror, it could literally be catastrophic to not exploit such flaws. Hawks would argue that it's your patriotic duty to pass such information onto the security agencies. Stuxnet, Flame and Duqu have all capitalised on zero day exploits with great success at disrupting Iran's nuclear program. It's to protect the children too. Or so the ideology goes. As the whether it's moral/ethical, those issues have been formalised by Obama's Special Assistant to the President and Cybersecurity Coordinator, Michael Daniel:-
- How much is the vulnerable system used in the core internet infrastructure, in other critical infrastructure systems, in the U.S. economy, and/or in national security systems?
- Does the vulnerability, if left unpatched, impose significant risk?
How much harm could an adversary nation or criminal group do with knowledge of this vulnerability?
- How likely is it that we would know if someone else was exploiting it?
- How badly do we need the intelligence we think we can get from exploiting the vulnerability?
- Are there other ways we can get it?
- Could we utilize the vulnerability for a short period of time before we disclose it?
- How likely is it that someone else will discover the vulnerability?
- Can the vulnerability be patched or otherwise mitigated?
This policy is called NOBUS in the US and is for "investing in groundbreaking cryptanalytic capabilities to defeat adversarial
cryptography and exploit internet traffic." Examples of it are Dual_EC_DRBG, cracking Diffie-Hellman and EternalBlue in Windows. Quoting, "as a general rule, tries to focus on exploiting vulnerabilities used in its targets’ software".
In summary, there's lots of money to be made. And you'd be contributing to your country's security as JFK asked of us all.
Update:
Latest (March 2019) NY Times estimate of this market now puts it at \$12B. Salaries >> \$200,000 working for companies like Darkmatter or NSO Group breaking WhatsApp and Skype traffic.
Update2:
Zerodium is now offering up to $2,500,000 per exploit. Ka-ching:-