I am trying to implement the correlation power analysis attack. I have a hardware AES for which I found a trigger which defines the start of the AES calculations. After that I performed an EM curves acquisition.
It is the first time that I have some traces so I have some questions about 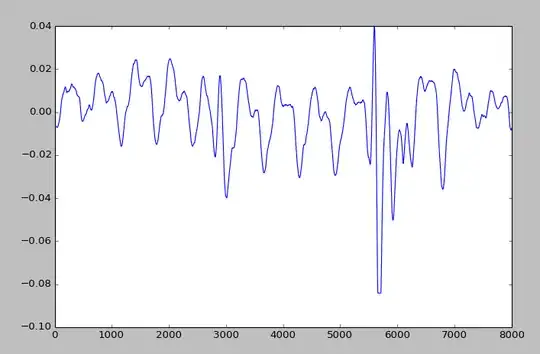 :
:
According to my trace, the x-axis is the time and the y-axis is the energy consumption. Is there any software that helps me to plot my trace more clearly and make them more comprehensive?
It is clear that I have some noise in my trace. So how to avoid that noise? which type of filter must do? Must I use a low pass filter or a high pass filter, I need to see my 10 rounds clearly to analyse? What are the steps that I must take?
Why there are an important possibility to make our attack in the first and last round of the AES?
Some explanation about CPA:'
We can use the Hamming Distance model in our CPA attacks. If we can find a point in the encryption algorithm where the victim changes a variable from x to y, then we can estimate that the power consumption is proportional to Hamming Distance(x, y)' I really don't understand the relation between the CPA and the hamming distance. Can anybody explain?Is there any software that helps me to make my CPA, given my curves?