I was wondering someting :
Doing a XOR with a fixed length key on txt files is not secure.
Basically : My key is "abc"
abc|abc|abc|abc|abc|abc
Thi s i s s ome dat a
THIS, is not safe.
BUT ! I was asking myself : why can't I just make a self generating infinite length key ? The user gives me a password, and I just hasing it to create a key, and whenever the length of the file is bigger then the key, i just re-hash the key itself to create a new one !
Example : Let's take a 192 Bytes message. Use SHA256 hashing algo create 48 Bytes keys.
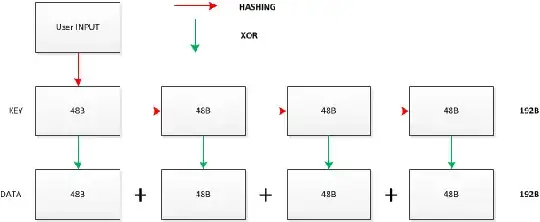
This solution resolve the ciphere vineger problem.
SO MY QUESTION ( here it is :p ) : Is this one safe ?
Thanks ! ~Amperclock