In practice, in situations like TLS, public key encryption will be used to encrypt a secret for encrypting the actual messages, as part of a hybrid cryptosystem. This is done because Asymmetric cryptography is significantly slower than symmetric cryptography.
However, there are other cryptosystems and applications that utilize public key encryption directly. As an example, ransomware is not concerned with how long it takes to encrypt something, and it benefits immensely from not possessing the decryption key.
There are also cryptographic logging schemes that make use of public key encryption directly:
Due to the forensic value of audit logs, it is vital to provide
compromise resiliency
and
append-only
properties in a logging system to prevent active attackers. Unfortunately, existing symmetric secure logging schemes are not
publicly verifiable and cannot address applications that require public auditing...
So whether or not public key encryption is used for key exchange or on the data itself is actually a matter of where the tools are being used.
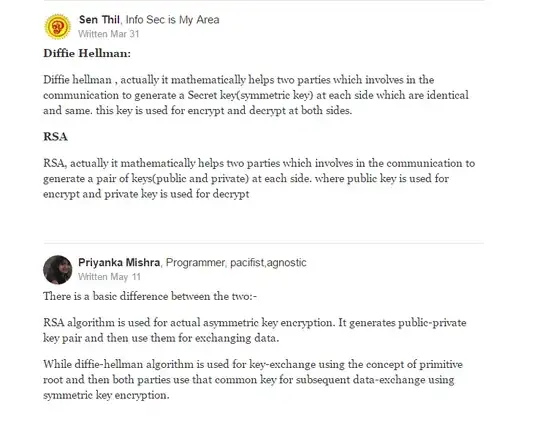
RSA and Diffie-Hellman are based on different but similar mathematical problems. While they both make use of modular exponentiation, exactly what they do/why they work is different. This is evident when you look at how to attack each one: RSA is threatened by integer factorization, while DH is threatened by discrete logarithms.
Additionally: DH is a "key exchange" algorithm, which is different then "public key encryption"; It allows you and another person to mutually arrive at the same piece of information, while nobody else can. It is more or less equivalent to using public key encryption on a random message. This is in contrast to public key encryption, where you get to select the message that both parties will be aware of.
Note that Diffie-Hellman can be turned into public key encryption.
tl;dr
Both use modular exponentiation to provide the main functionality (encryption/signature generation for RSA, key agreement for DH), but the underlying problem, the key pair generation and the security properties of the input/output are different