I am trying to understand the split mask countermeasure which is a masking method to avoid side channel attacks. Let's first describe the principle and then try to apply it to AES.
I found this paper which analyses this method. First, I will quote the presentation of the split mask countermeasure which is given in the second section:
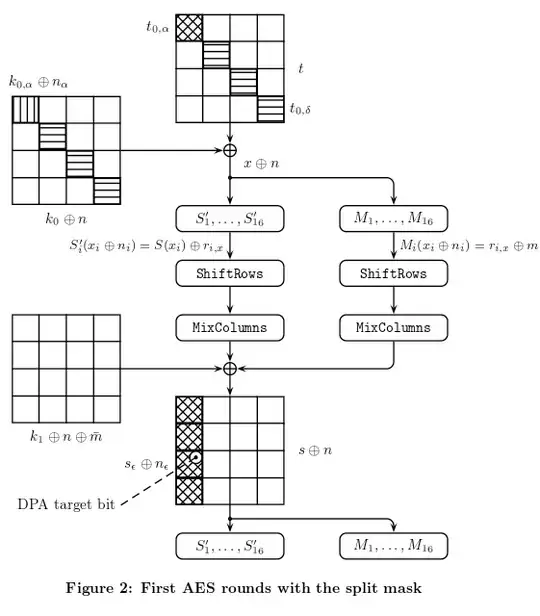
Let $S$ be an S-box with input $x$ and output $S(x)$ implemented as a lookup table. The split mask implementation of $S$ consists of a masked table $S′$ and a mask table $M$. These tables are defined as follows: \begin{equation} S'(x \oplus n) = S(x) \oplus r_x, \hspace{1cm}\\ M(x \oplus n) = r_x \oplus m \hspace{1cm}(1)\\ \end{equation}
This means that the input of the S-box is masked with $n$, and each output value is masked with an individual random value $r_x$. This gives the masked table $S'$. The set of output masks $r_x$ is also stored in the mask table $M$ so that \begin{equation} S'(x \oplus n) \oplus M(x \oplus n) = S(x) \oplus m \hspace{1cm}(2) \end{equation} holds for every input $x$. In other words, $m$ can be viewed as the output mask of $S$ that is split into two shares $r_x$ and $M(x \oplus n)$, the splitting being individual for each table entry.
The split mask countermeasure with a single mask table is claimed to thwart the 1-st order DPA attack. For this, the original description requires that $(2)$ should never be computed directly (i.e. appear as an intermediate value) during an algorithm execution.
The description seems clear to me except this sentence:
For this, the original description requires that $(2)$ should never be computed directly (i.e. appear as an intermediate value) during an algorithm execution.
So how should it be computed?
So let's consider we want to encrypt a block data using AES and the split mask countermeasure. We start by generating $n$, $m$ and 256 bytes $r_x$ to compute $S'$ and $M$.
But then, when we have to apply the $\texttt{SubBytes}$ operation during the algorithm, how to proceed?
In the same paper mentioned above it is said:
Other details of concrete implementations can be found in [10, 11, 12, 13]. In these papers the countermeasure is proposed for an optimized AES implementation with $8 \times 32$-bit lookup tables that are used to compute the S-box and the diffusion simultaneously.
but it concerns optimized $32$-bit implementation and I would like to simply implement it for a traditional $8$-bit version so it does not help me that much...