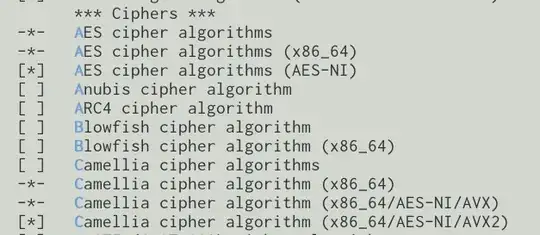
Modern processors support hardware acceleration for various crypto functions such as AES directly, or general vector operations which can be used in crypto functions, such as SSE SSE2 SSSE3 AVX.
On my machine, I can see the difference in speed between AES in software and in hardware, which gives speeds up to 5 times faster:
openssl speed -evp aes-256-cbc
openssl speed aes-256-cbc
(Note: I am using OpenSSL here only as an example, because it is easy to demonstrate.)
Also, the Linux kernel can be compiled with support for these functions as well. If so, all encryption in kernel space (for example IPsec, dm-crypt) can take advantage of these fast hardware instructions.
Again, the kernel compiled with AES-NI support is many times faster when uisng aes in software only.
I have noticed that there is also hardware support for the Camellia cipher and it looks as if Camellia could use the same instructions as AES, namely AES-NI and AVX.
However, I am unable to test/confirm this.
openssl speed camellia-256-cbc
openssl speed -evp camellia-256-cbc
I see no difference in speed when tested with OpenSSL and I suspect the hardware acceleration is not being used for Camellia.
My cpu supports all above mentioned instructions: AES SSE SSE2 SSSE3 AVX.
Is it possible to speed up Camellia by using hardware instructions on supported cpu, same as with AES?