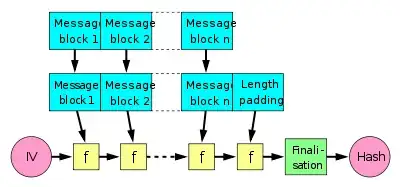
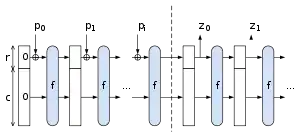
While Switch is right about the difference between Merkle–Damgård and Sponge constructions, I don't believe he is correct as to NIST's reasoning.
I happened to talk to a NIST cryptographer (John Kelsey) about this. He indicated that they selected Keccak not because they distrust the SHA-2 design (Merkle–Damgård is provably secure if the compression function is collision-resistant, and we have no reason to doubt the SHA-2 compression functions). And it's not to get greater crypto-diversity (even though it does that; the designs of SHA-2 and SHA-3 are quite different). Instead, John indicated that the most attractive thing they saw in Keccak was its flexibility.
While the sponge construction can be used to create a hash function, it can also be used to create other things, such as an XOF (Extensible Output Function; essentially as hash function with an arbitrary length output). NIST has standardized SHAKE-128 and SHAKE-256 as SHA-3 based XOF's. In addition, you can do other things with a sponge construction; it's quite possible that NIST will standardize those usages as well.