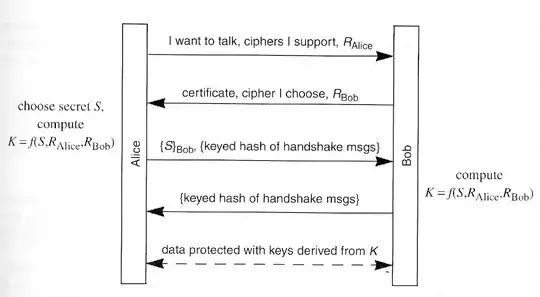
Both crypto.SE and security.SE have excellent Q&As about how TLS generates session keys (I have linked some at the bottom).
In reading these threads I'm having troubles with terminology since the following terms seem to be used with overlapping contexts, though they are clearly different concepts. Reading definitions is only partially helpful since they don't show the differences between their usages.
- pre-master secret
- master secret
- private key
- shared secret / session key
As I understand it, the pre-master secret is related to private keys, but is algorithm independent, and the master secret is (often?) used as the session key. But I'm sure there's more nuance to the definitions.
Related Questions:
- How does SSL/TLS work? [security.SE]
- What's the point of the pre-master key? [security.SE]
- What is the purpose of pre master secret in SSL/TLS? [crypto.SE]
- What's the difference between the long term key and the session keys? [crypto.SE]