I have a short (32-bit) message that needs to be authenticated. Due to the constraints of my platform, I would like to use Speck32/64 (32-bit block, 64-bit key) with a Matyas-Meyer-Oseas one-way compression function (due to its ease of implementation and because the input sizes match what Speck generates).
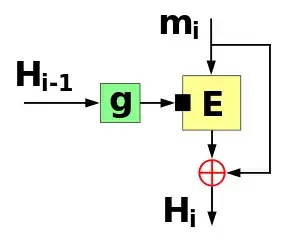
(Here, $E$ is Speck32/64, $g$ is a no-op, $m_i$ is the entire short message, $H_i$ is the tag, and $H_{i-1}=H_0$ is secret.)
However, my message is short enough that there won't be more than one iteration of the compression function; essentially, I would merely be XORing the output of the cipher with the plaintext. (Obviously, $H_0$ should remain secret!) I also don't care about the secrecy of the message, only its unforgability. Therefore, I would transmit the message in plaintext along with its equally-sized MAC.
Is it secure to give a third party the plain text that goes with a MAC? In other words, does the fact that the third party always knows the plaintext to a given tag weaken the security of the tag? If so, what needs to be changed to secure the message?