This is only a partial answer. It mostly addresses the fact that the proposed solution doesn't work generically. This is done by exhibiting secure schemes so that their composition in the proposed isn't secure. To be clear, the claim is about the generic security of the scheme, which is a requirement of the question. It is, in fact, very possible that the proposed construction is practically secure for specific instantiations. Like there are secure instantiations of Mac-then-Encrypt, e.g., CCM, next, I'll describe an alternative that potentially side-steps the previously mentioned issue. However, I have no proof that the alternative works generically, and it may potentially fail to some due to some other subtleties. I'll also discuss existing solutions that partially answer the requirements: they provide the required security guarantees at negligible computational costs but increase the signature size (by a hash), or they do not increase signature size but are not generic.
Context: The notion of “Collision resistance for signature” for signature, as described in the question, is also referred to in the literature as “Message Binding” (Boneh-Shoup, Brendel et al., Cremers et al..)
Generic security of the proposed solution
Assuming the reasoning below is not flawed, the solution suggested in the question does not appear to work generically, which is a question requirement. To do so, for any signature scheme $\Sigma = (\text{KGen}, \text{Sig}, \text{Vrfy})$ we will devise a secure PRP $E'_{\Sigma}$ so that breaking MBS security of the generic construction is easy. Which contradicts the generic security of the construction solely based on PRP security.
As a starting point, one question is what properties $E$ and $H'$ should have. Below are some observations, not to be interpreted as attacks but
as potential difficulties proving the security of the proposed construction.
Starting with $H'$. it must at least be collision-resistant. The trivial example where $H'(m) = 0, \forall m$ is a boring illustration of this. On the other hand, since the output of $H'$ is used to key a blockcipher, it seems necessary that $H'$ has some pseudo-random behavior and, therefore, is strictly more than collision-resistant. Alternatively, collision resistance could be enough if we accept working with the stronger ideal-cipher model (more on later).
Onto the PRP $E$: The first observation is that the PRP key is public, so it's unclear how to rely on PRP security. Secondly, it is possible that PRP security is not enough for the proposed solution to provide collision resistance generally. We can exhibit a PRP so that the construction fails to provide message-bound signature security (MBS). Details below.
Let $(m, m')$ be the message for which the attacker wants to create signature collisions under $pk$. We create another $E$, so the construction isn't secure. For simplicity, we consider a deterministic signing scheme, and we further define $\sigma_m$ and $\sigma_{m'}$ as signatures on $m$ and $m'$, respectively. Also, let $s$ and $s'$ be the block cipher output after applying the transformation(e.g.: $s = E_k(H'(pk|m), \sigma_m)$). We can now construct a new keyed PRP $E'$ that makes the construction insecure. $E'$ behaves just like $E$ and only with the only change that $$s = E'_k(H'(pk|m'), \sigma_{m'}),$$ and the original pre-image of $s'$ (say $v$) is mapped $E_k(H'(pk|m'), \sigma_{m'})$. In summary, we changed the following mappings under the key $H'(pk|m')$: $$(\sigma_{m'}, s'), (v,s) \to (\sigma_{m'}, s), (v,s')$$.
We observe that if $E$ was a secure PRP, then $E'$ is still a secure PRP. Namely, we haven't changed any guarantees expected from a PRP with a random key. However, the tuple $pk, m, m'$ breaks the MBS security of the generic construction. One thing to investigate is whether one could prove security in the ideal cipher model. Where for each key, each permutation behaves like a randomly chosen one... But I don't know...
Potential fix to the generic construction: TODO
The idea is to take inspiration from "re-encryption" type techniques. Concretely, the key to the PRP (permutation) is derived as a function of the public key, message, and signature $H'(pk,m,\sigma)$. Here, $H'$ is modeled as a random oracle with an image corresponding to the key space of the PRP. The rest goes as described in the question's proposal. Verification should verify the consistency of all values. Because of the “circular dependency” between the PRP key and input. It seems hard to play tricks on the PRP, as described above. However, this does not prove anything. Furthermore, I expect it to be hard to prove anything about this without employing ideal models.
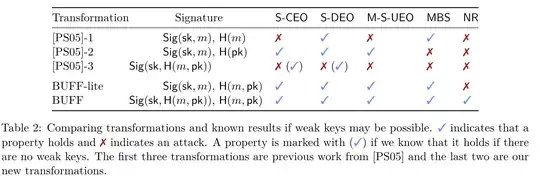
Existing work: the BUFF construction.
Cremers et al. introduced a (collection of) security notions titled Beyond UnForgeability Features (BUFF). This captures Unforgeability, Malicious Stronger, MBS (collision resistance), and Non-assignability (NS). NS captures the inability to sign a message the adversary does not “know.” There are two generic transformations proposed $(\text{Sign}(sk, m), H(pk,m))$ and $(\text{Sign}(sk, H(pk,m)), H(pk,m))$.
BUFF security appears to be a desirable feature of newer post-quantum schemes. Cremers et al. studied the BUFF security of round 3 NIST finalists, and newer candidates have also been analyzed by Aulbach et al..
On signature size: Both generic transforms inevitably increase signature size. However, for a specific scheme, the simpler transformation of Pornin and Stern, a.k.a PS-3, is shown to be enough to achieve BUFF security without increasing signature size. PS-3 is defined as $(\text{Sign}(sk, H(pk,m))$
Pornin-Stern transforms
Specifically for MBS security, the PS-1 transform provides MBS security (Collision resistance) under collision resistance of the hash function. PS-1 is defined as $(\text{Sign}(sk, n), H(m))$. However, the signature size must increase.
The picture below (from Cremers et al.) recaps the various constructions and their security.