I am looking at ways to blind an ECDSA signing key (and verification key respectively).
Looking at proposed solutions like the IETF KBSS draft, and the IETF ARKG draft it seems that the ECDSA key blinding requires a multiplicative blinding with a blinding value $b$ that cannot be controlled by an attacker (and I assume malicious user). Given an original key pair $(d, Q_d)$ the blinded key pair is computed as $(b \cdot d, b \cdot Q_d)$.
However, neither ARGK or KBSS details how this multiplication is to be achieved (secure hardware may limit access to the private key). In SECDSA, Verheul proposes an approach where a multiplication can be done without learning the private key as follows:
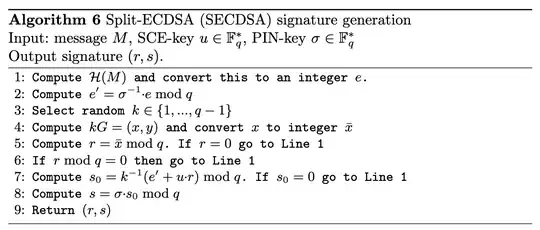
The SCE-key and PIN-key represent two private keys with the former being hardware protected. Seemingly, the PIN-key could be replaced with a blind to create a blinded signing key ($\sigma \cdot u$) and a blinded public key ($\sigma \cdot uG$).
I understand how the proposed algorithm can generate a signature using the blinded private key that can be verified using the blinded public key. But the paper does not give any formal security proof. Is the above proposal secure if $\sigma$ cannot be chosen freely? Is anyone aware of similar approaches? Is the approach in Algorithm 6 novel in these sense that it can blind a private key without having to learn the value of the original private key?
Update: There seems to be similar techniques as the one presented above. Threshold ECDSA was discussed earlier in the 54874 post, and essentially presents ways to compute a signature using two different private keys as input. For instance, Lindell 2017 as well as MacKenzie & Reiter 2004 discuss a threshold signature ECDSA scheme that relies on an approach that is similar to the multiplicative blinding use case. Adopting their work to a setting where a single user controls both keys is easy and seems to be the exact same algorithm as algorithm 6 in the Verheul paper.