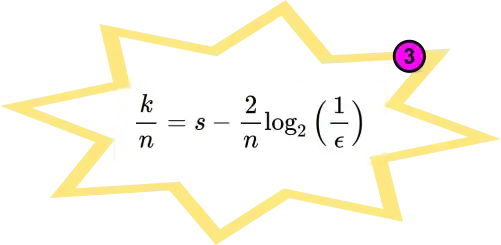Updates
As discussed in the answer (Caveats) and in the comments, a drawback of what is described below is the independence assumption between the extractor and the seed. This is rather unrealistic in real life since for instance SHA256 may have been used to generate an ephemeral DH scalar via a PRNG and used as well in (un-seeded) HMAC to derive the shared secret. Two papers dealing with these considerations:
I will assume the question is about computational randomness extraction; in particular, we are not in the realm of the impossibility result of extracting randomness with a deterministic function. Additionally, I will assume that the entropy source is independent of the hash function.
With those two assumptions, a sufficient condition (more like assumption) for the hash function is that the hash function "behaves" like a random oracle.
Now, it is well known that a single hash function cannot realize a random oracle. Therefore, the notion of "behave like a random oracle" is not appropriate and cannot be interpreted in the sense of indistinguishable from a random oracle. Instead, we can really on the notion of "Indiffernetiability from a random oracle".
Indifferentiability: The indifferentiability framework introduced by Maurer, Renner and Holenstein describes indifferentiability as a generalization of indistinguishability. Summarized: Let $T$ be a cryptosystem using an idealized but publicly available resource $R$ to realize the ideal cryptosystem $T$. $S$ is said to be indifferentialbe from $T$, if there exists a simulator $\mathcal{S}$ such that "translates" $R$ from the ideal resource $T$. Said differently, for any (efficient) distinguisher $D$, it cannot distinguish between an interaction with $(R, S)$ and with $(\mathcal{S}, T)$.
The notion comes with a composition theorem that essentially says that for any cryptosystem $\mathcal{C}$ proven secure when using $T$, and if $S$ and $T$ are indifferentiable., then $\mathcal{C}$ is also secure when using $S$ (There are some caveat).
This is useful in this context since, the framework has been applied to hash functions(Sponges), HMAC.
Hugo Krawczyk also discusses here the role of indifferentiability for the security of HKDF assuming a fixed, zero salt.
Caveats: Now, the arguments above can be contested for a number of reasons: 1) Independence assumptions, 2) Idealizations.
Because we assume independence of the source and the underlying hash function (or compression), the answer is not as general as in the case of HKDF with random salts. But the question doesn't state that this assumption is not acceptable. Indifferentiability still requires some idealization (of the underlying compression function or block cipher). However, the value can be seen as a minimization of assumptions: idealizing a compression function seems to be less strong than doing that for a full hash function with structure, etc...
To be as general as possible, I would still use a salted HKDF instead of a single hash function or even HKDF with a zero salt.