A question I came across describes a scenario of an information system in a clerical office and states-
"Identify the sets of S={subjects}, O={objects} and P={privileges} for the above systems of the manufacturing organisation, and model the case using an access control graph."
Further, the question says-
"Your graph should indicate links representing overriding or modifying operations."
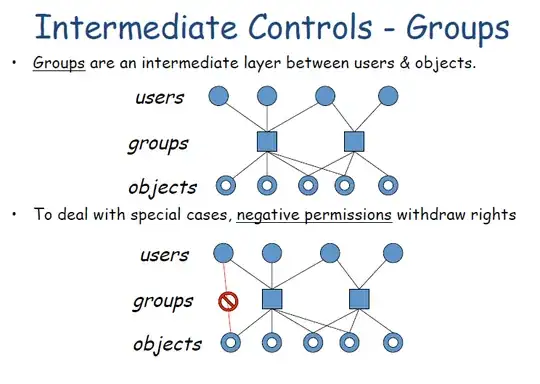
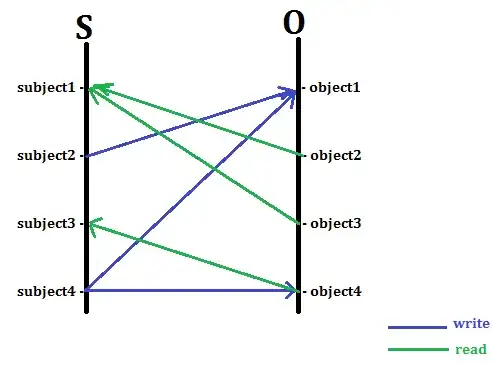
What is a access control graph? I came across the following 2 diagrams, the latter depicts the BLP model. Which one should be used in this context?