It's about 64.
Notwithstanding intergalactic adventures, it's a little akin to grasping a slippery eel. So we only have anecdotal evidence to draw upon. One use of a small $\epsilon$ is in the generation of true random numbers.
- A relevant document to TRNG design is DRAFT NIST Special Publication 800-90C, Recommendation for Random Bit Generator (RBG) Constructions,
August 2012, which is predicated on good output as $\epsilon \leq 2^{-64}$.

(Strangely, this definition has vanished in the latest draft.)
- NIST Special Publication 800-90B, Recommendation for the Entropy
Sources Used for Random Bit Generation, January 2018 says

when talking about TRNG health tests.
A CSPRNG built upon AES in counter mode is currently a standard form. The output sequence stands a good chance of being distinguished after $2^{64}$ blocks. We still accept that risk given the likelihood of generating 2 Zettabytes of data.
ID Quantique's Technical Paper on Randomness Extractor, Version 1.0, September 2012 has mention of them achieving $\epsilon < 2^{-100}$.
Bruno Sanguinetti, Anthony Martin, Hugo Zbinden, and Nicolas Gisin, Quantum Random Number Generation on a Mobile Phone, Group of Applied Physics, University of Geneva, Genève 4, CH-1211, Switzerland state they achieve $2^{-320} \leq \epsilon \leq 2^{-270}$ depending on photosensor technology.
With regard to items 4 & 5: It's trivial to generate a minuscule $\epsilon$ by simply altering the entropy input to output ratio on the extractor algorithm. I would take these values as atypical examples of a negligible number.
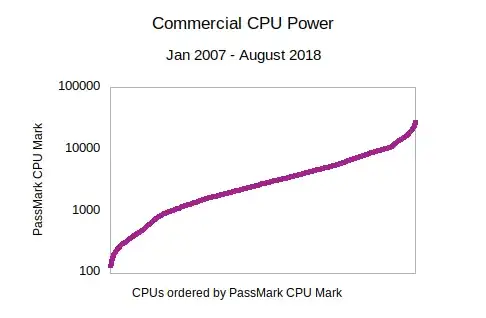
Finally this PassMark chart shows the continuation of Moore's Law into the future, especially as new nodes are developed such as IBM's 5nm process, and core scale out:-
So ignoring outliers at $2^{-20}$ and $2^{-320}$, NIST remains of the view that a bias of $2^{-64}$ is still safe. Hence answer = 64.


