This is actually possible in practice because to us, human beings, a "meaningful message" can be a file.
Now, depending how we encrypt our files, we have more or less slack variables at hand to play around with the resulting ciphertexts.
Ange Albertini played a lot with file formats and he actually has a PoC where he encrypts given images into other files, even valid images... Or where he encrypts a JPG into a PNG if using AES and into a PDF if using 3DES... Or even worse!
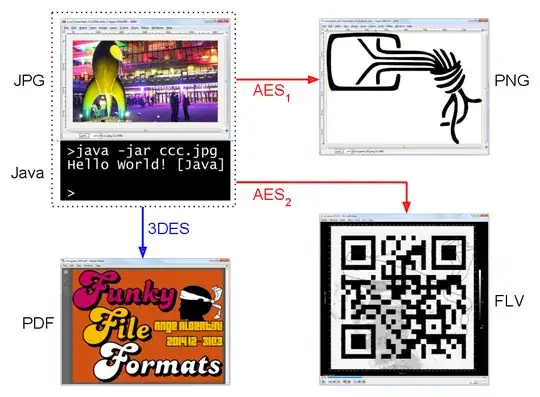 (image by Ange Albertini, CC3.0BY)
(image by Ange Albertini, CC3.0BY)
How comes? Well, this is mostly done by abusing the way the modes of operation work, as well as the way the file formats work.
When you encrypt a file using AES CBC, for instance, you can choose your IV, which means that you can control the first 128 bits of your ciphertext. Furthermore you can also append any plaintext data at the end of your ciphertext, and it will get encrypted when you decrypt your ciphertext, but it also means that you can obtain its corresponding ciphertext so that it gets decrypted when you encrypt your plaintext appended with that ciphertext...
With this two details you already have plenty of room to play around with the file formats in a way that would produce valid files when encrypted/decrypted!
Now, a question that was not addressed by Ange is whether this is secure...
Well, as long as you are appending encrypted data or that you are not reusing your IVs, this does actually protects the content of your files (especially Ange's limited deniability example), as long as your secret key remain secret... (But it might be a problem in the case of CBC, depending on your use of the cipher, as it mandates most of the time the IVs to be unpredictable, unlike CTR where it suffices to have unique nonces.)
So, is it possible to do the same in the other direction, decrypting into two different files given different keys? Well, if you can have different IVs, then yes, it is possible using the same kind of tricks that Ange used.
In the end, is this related to the way the actual ciphers work? No, not at all. This is not a cryptographic property, but a consequence of the file formats' malleability.
