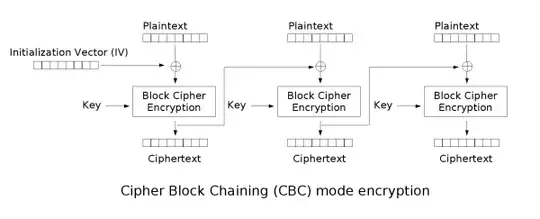
Let's say a 1MB file has many many consecutive null-bytes 128-bit blocks. Then, as AES works with blocks, the encrypted file will also have recurrent 128-bit-long patterns of aes_encrypt(000...0) (where 000...0 is a 128-bit long null block).
How isn't this a weakness?
As null-bytes blocks is very frequent in files, we could easily recognize "oh this recurrent pattern in cipher is certainly the result of the encryption of 128 null bits".
Then a lookup table:
Key Cipher of null 128-bits
----------------------------------------------------
Hello a8ff00ac..ff6b
easypassword b20fa312..ae27
could help to find the key, isn't it possible?
Is the fact it "works in blocks" not a weakness?