In the document http://web.cs.ucdavis.edu/~rogaway/papers/eax.pdf (p. 7) Rogaway et. al. state that EAX is not a generic composition of an encryption and an authentication method.
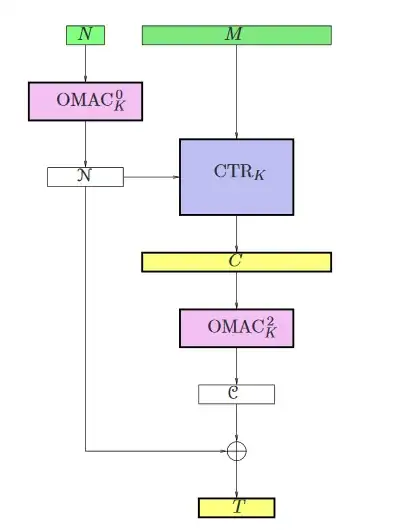
The EAX algorithm is given in the following Image:
(the image is taken from p. 7 of the referenced paper and simplified by omitting the associated data)
So, the plaintext M is encrypted by a CTR block cipher mode and the resulting ciphertext is authenticated by an OMAC tag. So far, this looks pretty much like an encrypt-then-authenticate based generic composition. The only thing particular here is, that the tag $\mathcal{C}$ isn't the final tag but is XORed by the tagged nonce $\mathcal{N}$.
My questions are:
- Why isn't EAX considered to be a generic composition ?
- Would EAX be a generic composition of the block cipher mode encrytion and the OMAC authentication, if $\mathcal{C}$ would be used as authentication tag T ?
Added: Actually, I think the answer depends on the point of view.
(1) Proof of security: Security proofs for generic compositions assume that two different, independet keys are used for encryption and authentication. As EAX uses the same key for both, security results for generic compositions don't apply to EAX. So in this point of view EAX is not a generic composition.
(2) Design principle: When one tries to classify AE algorithms, one can look how they are designed. By design, a generic composition is an algorithm that runs an encryption and an authentication algorithm in a (generic) order that is independent from the primitives: E.g. Encrypt-then-Authenticate, Authenticate-then-Encrypt, etc. In this point of view I would consider EAX (as well as CCM) as a generic composition.