Respondents have well addressed the futility of trying to brute force a 256 bit AES key. It's hard. But I want to focus on your last paragraph.
Would it be possible to take these algorithms e.g AES and just change the key size from 256 to 512 or 1024? I mean the algorithm is well tested, you would just have to modify the key and block size.
Actually, no you can't. AES is well tested and a number of people have studied it. It works as a fait accompli by virtue of having been designed as a cohesive unit, with all sub operations working perfectly together. This is AES:-
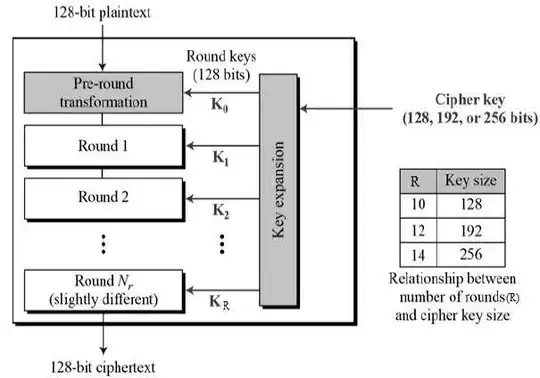
The rounds and the key expansion are the clever bits. A key of predetermined length is expanded so that derivatives of it can be introduced at each round in the algorithm. The key expansion is carefully designed to maximise entropy, avoid weak states and collisions. And they don't repeat so all round keys will be different. The algorithm is proven to work for 10 /128, 12 /192 and 14 /256 round /key permutations. And they also all produce fixed width (128 bit) round keys which contributes to having a 128 bit block width. That's invariant.
If you decide to upgrade AES to a 768 bit block width for uber security, you can't realistically. How would you expand a key of some length to produce repeated but different round keys of 768 bit width? The key scheduling is one of the most important parts of a cipher. It would mean a complete rewrite of the key scheduler.
And the individual round algorithm would have to be expanded to 768 bits. The following isn't from AES, but it has beautiful symmetry and illustrates to difficulty of arbitrary block width expansion:-
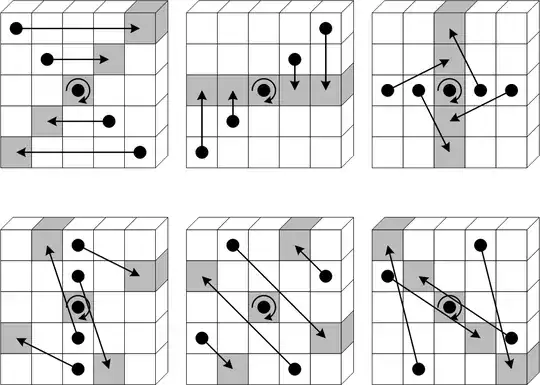
Imagine this table containing all the bits in a round. It's 5 x 5 bits, and you can see the careful way the bits cycle round symmetrically. This adds to diffusion and the avalanche effect. Now imagine adding another row to create a 5 x 6 table. For a start, there's no middle bit in an even number of bits. You'd need to completely redesign the bit permutation sequence.
All the words above are a long winded way of saying that if you tried upgrading AES or any other cryptographic primitive, you'd have to completely rewrite it from scratch. So it's no longer well tested and you're back at square one.

