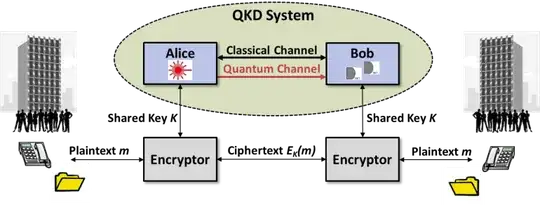
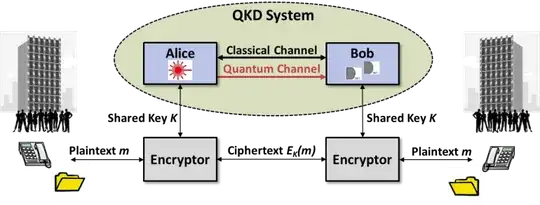
There are many diagrams out there explaining how quantum key distribution works on a physics /optics and mathematics level. I understand these explanations fairly well so I'm not asking about the underlying principles. This is one of the few that actually features people on it (although they seem to be fairly incidental to the usage):-
As I understand it, the machines only transmit keys not actual business data. I appreciate the exchange is done with one time pads, but is it like Diffie–Hellman key exchange otherwise, but only between fixed machines /servers? Do they replace entering AES keys transmitted over the phone /fax? Since AES is hard to break, surely the keys don't need replacing every hour? And do they then operate in pairs, because two is only a network from a marketing perspective. They can't control the log in into my desktop computer can they? And wouldn't all the desktops have to be interconnected with fibre optics rather than Ethernet? The latter is probably a rather naive question.
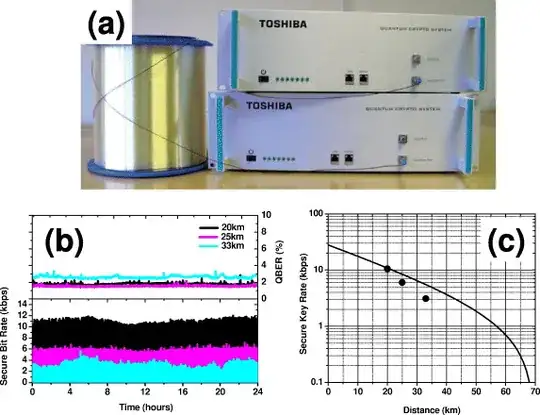
This additional image clearly shows the transmission of secure encryption keys through a Toshiba quantum network:-
At a separation of 20Km, the devices are generating /exchanging keys at a rate of 10 kbits/s. Why as that's 40 no. 256 bit AES keys each and every second? What exactly does someone do with 140,000 unbreakable AES keys per hour? Even more ridiculously, that's a million new keys in a single business day.
I'd appreciate an answer from a operational perspective, although I realise that this is firstly a cryptography theory site. So what's it for?
I looked at Quantum key exchange skepticism/confusion and a simulated network, but both were unfruitful.