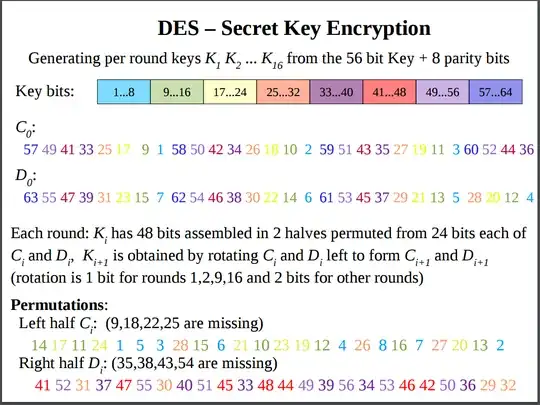
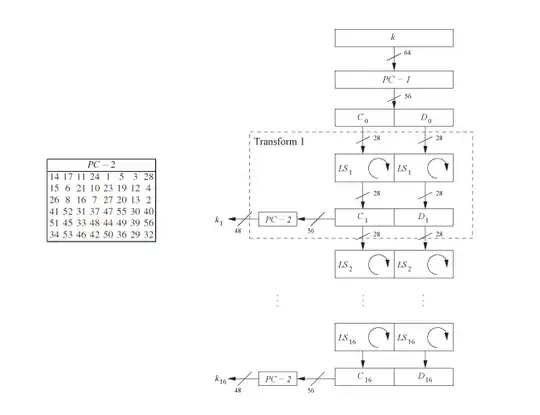
I am reading over a slide that I found online regarding the DES algorithm for encryption and I am a little confused about the per round key generation. From the slide below, I understand that each per round key is obtained by shifting left either 1 or 2 bits depending on the round. The thing I do not understand is the permutations for Left half C_i and right half D_i
In the slide, it says that the left half C_i is 14 17 11 24 1 5 3 28 15 6 21 19 23 19 12 4 26 8 16 7 27 20 13 2. Are the numbers in this example random? A textbook I am reading also uses the same numbers for round C_i and I cannot see the connection here. C_0 does not contain 14, so I am not really sure how left shifting bits causes the 14 from D to go to C. Am I misunderstanding the problem here?