If you use the OTP it has been used since its invention you will not get away with it. But there is a way that you can beat an attacker (Eve).
For the purpose of sending only text we will add a comma, full stop and a space character into an alphabet and randomise it. This will be the initial key that Alice and Bob share.
The possible permutations for the randomisation are P29 = 29! = 29 x 28 x…..2 x 1.
(Alphabet: P26 = 26! = 26 • 25 …….. 3 • 2 • 1 = 403,291,461,126,605,635,584,000,000)
This initial key needs to stay secret and only shared by Alice and Bob.
Below the image shows one of the possible permutations(P29); two messages we encrypted with two ciphers that displays the hex and decimal values we used to replace our text, a full stop and space characters.
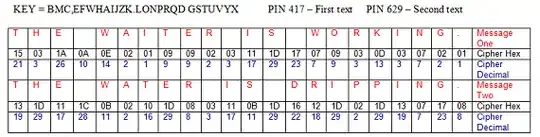
Before Alice starts to encrypt her message she creates a pin number (we used 3 digits) that will be used to create the cipher. The first step she does is moving the starting point of her first permutation by using the first number of the pin.
STEP = EFWHAIJZK.LONPRQD GSTUVYXBMC, Position moved by 4 (T = 21)
Moving to the end of the string looking for the next character. When reaching the end she returns to the start
of the string and moving again the position according to the next pin number.
STEP = FWHAIJZK.LONPRQD GSTUVYXBMC,E Position moved by 1 (H = 3, E = 26)
STEP = K.LONPRQD GSTUVYXBMC,EFWHAIJZ Position moved by 7 (space character = 10)
STEP = NPRQD GSTUVYXBMC,EFWHAIJZK.LO Position moved by 4
STEP = PRQD GSTUVYXBMC,EFWHAIJZK.LON Position moved by 1
STEP = TUVYXBMC,EFWHAIJZK.LONPRQD GS Position moved by 7
STEP = XBMC,EFWHAIJZK.LONPRQD GSTUVY Position moved by 4
STEP = BMC,EFWHAIJZK.LONPRQD GSTUVYX Position moved by 1
STEP = HAIJZK.LONPRQD GSTUVYXBMC,EFW Position moved by 7
Step = ZK.LONPRQD GSTUVYXBMC,EFWHAIJ Position moved by 4 (full stop = 1)
What Alice did is creating a string of random numbers which are as random as characters picked by an operator. Each number can represent any of the 29 characters in our randomised extended alphabet (1/29). Linguists too will have a problem to identify pattern that language holds since the randomization of our extended alphabet has destroyed them; and recording differences between characters doesn’t give anything away about the frequency of characters.
Now Alice can email her message and the pin code (of no use to an attacker without the correct permutation) and Bob can reverse it by using the pin code.
For a system that can encrypt text (no restrictions on languages), images, media files etc use a randomized ASCII (extended 256).
